A-180E Electronic Key Management System
The more keys to manage, the more difficult it is to keep track and maintain the desired level of security for your buildings and assets. To efficiently and securely manage a large amount of keys for your company premises or vehicle fleet can be a huge administrative burden. Landwell electronic key control systems will help you.
Landwell A-180E Electronic Key Cabinet
Control, track your keys, and restrict who can access them, and when. Recording and analyzing who is using keys—and where they’re using them - enables insights into business data you may not otherwise gather.
Advantages

100% Maintenance Free
With contactless RFID technology, inserting the tags in the slots does not result in any wear and tear.

Enhanced Security
Keep keys onsite and secure. Keys attached using special security seals are individually locked in place.

Touchless Key Handover
Reduce common touchpoints between users, minimizing the possibility of cross-contamination and disease transmission among your team.

Accountability
Only authorized users are able to access the electronic key management system to designated keys.

Key Audit
Real-time gain insight into who took what keys and when, whether they were returned.

Increased efficiency
Reclaim time you'd otherwise spend searching for keys, and reinvest it into other important areas of operations. Eliminate time-consuming key transaction record-keeping.

Reduced cost and risk
Prevent lost or misplaced keys, and avoid pricey rekeying expenses.

Save Your Time
Automated electronic key ledger so your employees can focus on their main business

Integrating with existing systems
With the aid of the available APIs, you can easily link your own (user) management system with our innovative cloud software. You can easily use your own data from your HR or access control system, for example.
Features
- Big, bright 7″ Android touchscreen
- Keys are securely attached using special security seals
- Keys or keysets are individually locked in place
- PIN, Card, fingerprint access to designated keys
- Keys are available 24/7 to authorized staff only
- Instant reports; keys out, who has key and why, when returned
- Remote control by the off-site administrator to remove or return keys
- Audible and visual alarms
- Networked or Standalone
Idea for
- Campus
- Police and Emergency Services
- Government and Military
- Retail Environments
- Hotels and Hospitality
- Technology Companies
- Sports Centres
- Healthcare
- Utilities Factories

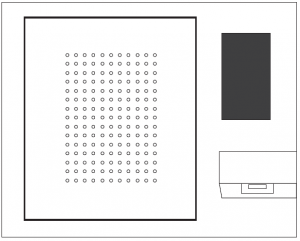
Key Panel
The locking receptor strips lock the key tags in position and will only unlock them to users authorized to access that particular item. So, Locking Receptor Strips provide the highest level of security and control for those who can access protected keys, and it's recommended for those requiring a solution of restricting access to each individual key.
Dual-color LED indicators at each key position guide the user to quickly locate keys, and provide clarity as to which keys a user is allowed to remove.
Smart Key Tags
The Key Tag is the heart of the key management system. It is a passive RFID tag, which contains a small RFID chip that allows the key cabinet to identify the attached key. Thanks to the RFID-based smart key tag technology, the system can manage almost any form of physical key and therefore has a wide range of applications.


User Terminal
The embedded Android user terminal is the field-level control center of the electronic key cabinet. Big, and bright 7-inch touchscreen makes it friendly and easier to use.
It integrates with smart card readers and biometric fingerprint readers, allowing the vast majority of users to use existing access cards, PINs and fingerprints to gain access to the system.
User Credentials
Sign in securely & authentication
The A-180E system can be operated in various ways, with different registration options, via the terminal. Depending on your requirements and situation, you can make the best choice – or combination – for the way in which users identify themselves and use the key system.





In case of Power-Off
In case of power failure, or other special circumstances, you can use the emergency key to open the cabinet door and manually take out the key.
Data sheet
Dimensions: W500 * H400 * D180 (W19.7” * H15.7” * D7.1”)
Weight: 18Kg net
Power: ln: AC 100~240V, Out: DC 12V
Consumption: 30W max,Typical 7W idle
Network: 1 * Ethernet
USB Port: Port outside the box
Certificates: CE,FCC,RoHS,ISO9001
Administration Features
The cloud-based management system eliminates the need to install any additional programs and tools. It only needs an Internet connection to be available to understand any dynamics of the key, manage employees and keys, and grant employees the authority to use the keys and a reasonable use time.
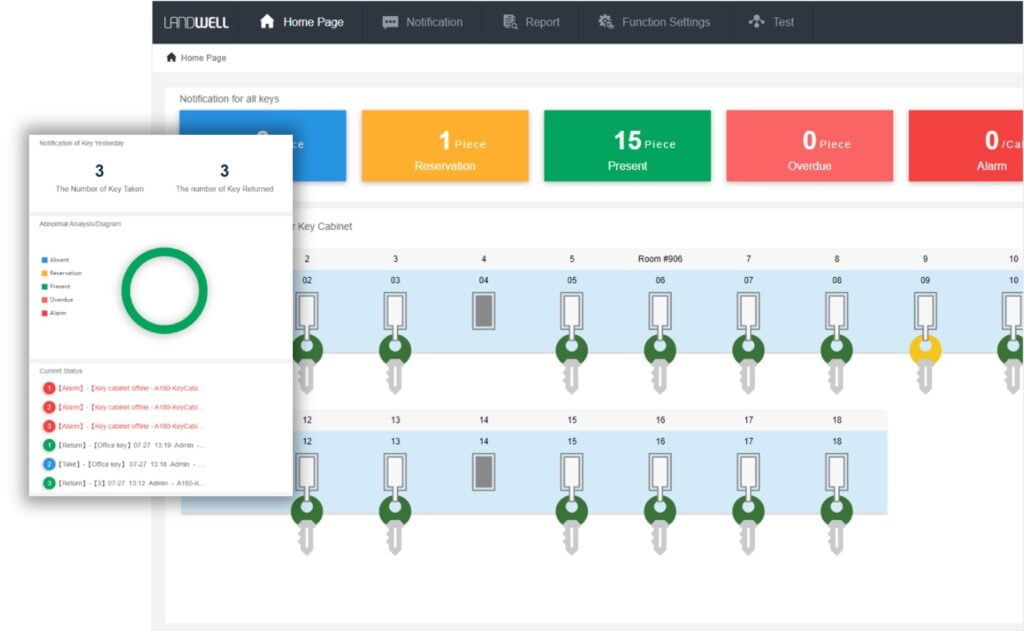
Administration Features
The system allows configuring key permissions from both user and key perspectives.


Multiple User verification
Same as The Two-man rule, is a control mechanism designed to achieve a high level of security for especially physical keys or assets. Under this rule all access and actions requires the presence of two authorized people at all times.
Multi-Factor Authentication
Is an additional level of security that uses multiple pieces of information to verify your identity. The system requires at least two credentials to authenticate a user’s identity.
Who Need Key Management System
The electronic key management systems have been applied to a range of sectors across the world and help to improve security, efficiency and safety.
- Government
- Hotels
- Auto Deals
- Banking and Finance
- Campus
- Property
- Healthcare
- Real Estate Leasing
- Office
- Fleet management

An intelligent key cabinet might be right for your business if you experience the following challenges:
- Difficulty keeping track of and distributing a large number of keys, fobs, or access cards for vehicles, equipment, tools, cabinets, etc.
- Time wasted in manually keeping track of numerous keys (e.g., with a paper sign-out sheet)
- Downtime looking for missing or misplaced keys
- Staff lack accountability to look after shared facilities and equipment
- Security risks in keys being brought off premised (e.g., accidentally taken home with staff)
- The current key management system not adhering to the organization’s security policies
- Risks of having no re-key the entire system if a physical key goes missing
Contact Us
Wondering how key control can help you improve business security and efficiency? It starts with a solution that fits your business. We recognize that no two organizations are the same - that's why we are always open to your individual needs, willing to tailor them to meet the needs of your industry and specific business.




